
In the landscape of data analysis, anomalies represent unexpected deviations that can significantly impact various sectors. Understanding these anomalies is crucial for industries aiming to enhance their operations and mitigate risks.
Understanding Anomalies
Anomalies in deep learning are data points or patterns that don't fit the usual crowd. These oddities can be critical for industries ranging from finance to healthcare. Spotting anomalies might catch a fraudulent transaction or find a defect before it rolls off the production line.
There are several types of anomalies:
- Point anomalies: Individual data points that stand out
- Contextual anomalies: Depend on their context, like unseasonal weather patterns
- Collective anomalies: Groups of out-of-place data that might blend in individually
The impact of detecting these anomalies is significant. For financial institutions, identifying fraudulent transactions early can save millions. In healthcare, anomalies in patient data can signal the onset of a disease. In manufacturing, faulty products can be flagged before reaching consumers.
For example, an energy company monitoring its grid can use anomaly detection to indicate faulty lines or theft of service. Early detection helps keep the system running smoothly and prevents costly downtime.
The approach to detecting anomalies often involves creating a baseline of "normal" data patterns. Once the norms are understood, anything that veers off track is flagged for deeper analysis.
Deep Learning Techniques
Deep learning techniques such as Autoencoders, Variational Autoencoders (VAEs), and Generative Adversarial Networks (GANs) have emerged as effective tools for unveiling anomalies.
Autoencoders compress data into a lower-dimensional space and then try to rebuild the original data. If the reconstruction has errors, it might indicate an anomaly.
VAEs add a probabilistic element, providing more nuanced insights into whether a data point is an outlier. They excel in providing a measure of confidence, which is useful in domains where understanding the likelihood of anomalies is crucial.
GANs pit two neural networks against each other—a generator that creates data and a discriminator that evaluates it. When used for anomaly detection, any data that the generator struggles to mimic convincingly could be abnormal.
These deep learning models handle complex, high-dimensional data with ease, unlike traditional methods. They don't need pre-labeled datasets of anomalies to function effectively, working by learning the 'normal' so deeply that deviations become apparent.
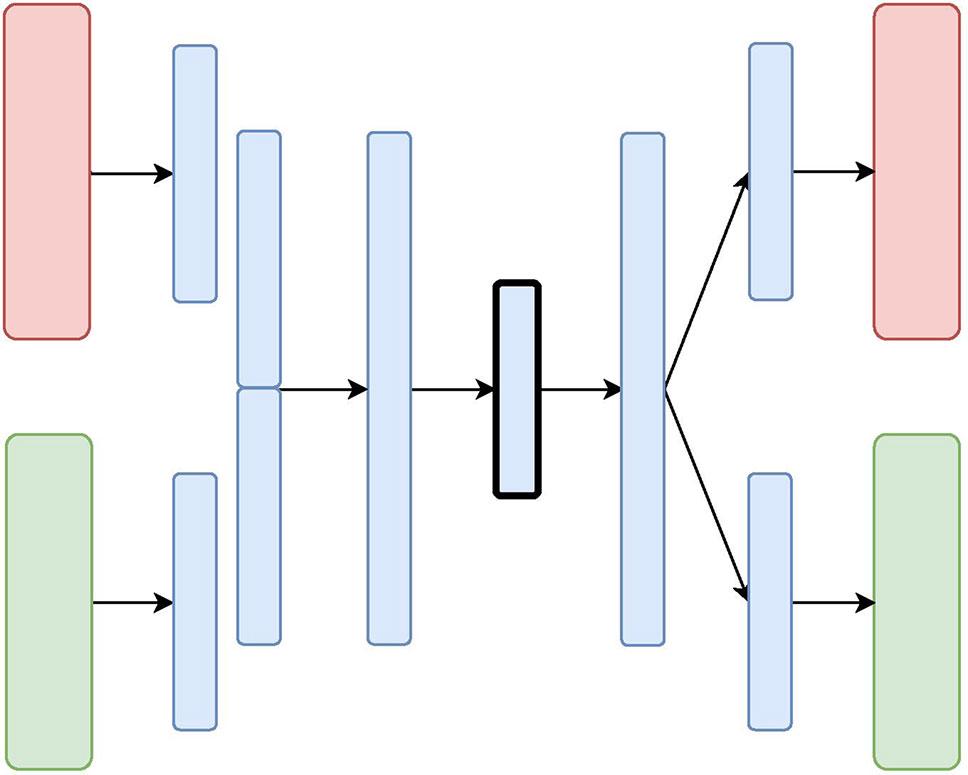
Model Selection and Application
Choosing the right model for anomaly detection involves matching their strengths to the tasks at hand. The choice depends on data characteristics and application needs.
| Data Type | Recommended Model |
|---|---|
| Time-series data | Sequence-to-Sequence networks |
| Spatial data | Convolutional autoencoders |
| Moderately-sized datasets with complex variability | Variational Autoencoders |
| High-dimensional data (e.g., cybersecurity) | GANs |
Traditional methods like Isolation Forests or One-Class SVMs can be useful when resources or data are limited, providing quick anomaly detection with less computational overhead.
The process of selecting a model is tied to the problem you're solving. For example, in medical diagnostics, the robustness of VAEs in managing uncertainty and the ability of convolutional architectures to handle image data are particularly useful.
Deployment and Implementation
Deployment of anomaly detection models begins with setting up the right environment, which might require powerful computing resources or cloud services to scale dynamically.
The training phase involves feeding the model with quality data in substantial amounts to fine-tune its anomaly detection capabilities. Be mindful of overfitting, which can sway the model away from discerning true anomalies.
Integration into existing systems should be seamless, with anomaly detection becoming a quiet proponent of your systems' defenses. This involves scripting APIs to communicate between components and ensuring real-time data flow.
Challenges in deployment include:
- Latency: Optimizing model performance to analyze data swiftly
- Data privacy and security: Especially when working with sensitive information
- Interpretability: Explaining findings in a user-friendly manner to stakeholders
Successful deployment involves iterative experimentation and monitoring. Periodically retraining the model on new data keeps its skills sharp, adapting to evolving patterns of normalcy and anomaly.
Evaluating Model Performance
Several metrics are used to measure a model's ability to detect anomalies effectively:
- Precision: Represents the portion of identified anomalies that are actually anomalies
- Recall: Measures how many actual anomalies are spotted
- F-score: Blends precision and recall into a single metric
- Matthews Correlation Coefficient (MCC): Useful for imbalanced datasets, synthesizing all performance aspects
Interpretation of these metrics is crucial. Too many false positives? Focus on precision. Missing critical anomalies? Bolster recall. Continuous monitoring and retraining based on new data streams can enhance the model's capacity to anticipate emerging patterns and evolving threats.
"Evaluating model performance in anomaly detection isn't about setting static benchmarks but fostering a dynamic growth mindset. It's about adapting models to the constantly changing landscape of anomalies."
Photo by lukechesser on Unsplash
Recognizing and addressing anomalies is about harnessing the power of data to drive informed decisions and safeguard against potential disruptions. This approach transforms anomaly detection into a strategic asset, guiding businesses towards greater resilience and success.
- Hawkins D. Identification of Outliers. Chapman and Hall; 1980.
- Chandola V, Banerjee A, Kumar V. Anomaly detection: A survey. ACM Computing Surveys. 2009;41(3):1-58.
- Pang G, Shen C, Cao L, Hengel AV. Deep learning for anomaly detection: A review. ACM Computing Surveys. 2021;54(2):1-38.


